Users, roles, and RBAC
Keep Open Mercato secure by curating roles, features, and user-specific overrides. The Auth module ships dedicated admin pages for both roles and users so you can adjust access in one place.
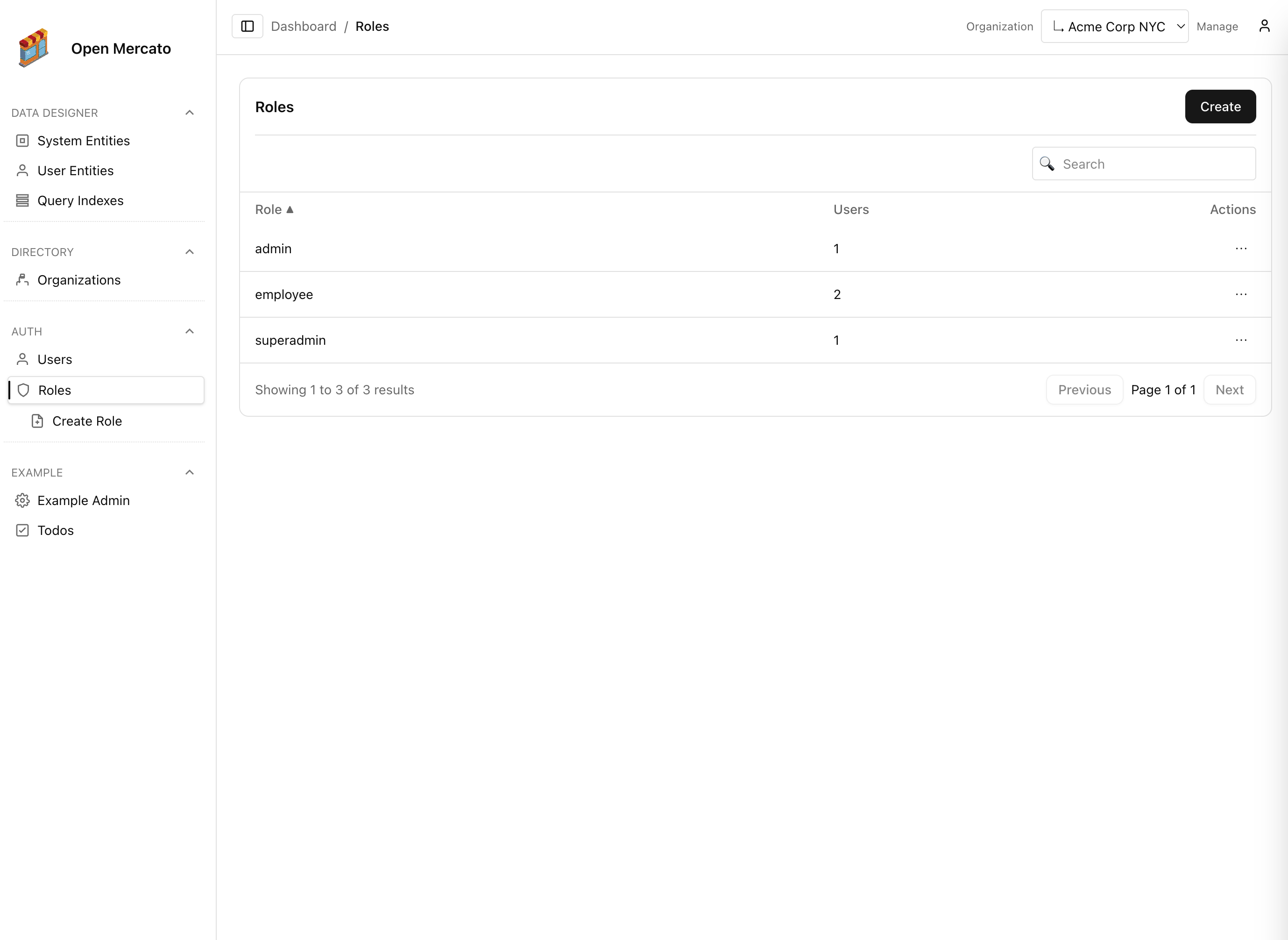
Manage role catalogs
- Navigate to Auth → Roles to review every role in the active tenant. New installations seed
adminandsuperadminroles with broad access, including organization management and dashboard visibility. - Inspect role details to see the features that role grants. Features follow the
<module>.<action>convention and mirror each module’sacl.ts. Toggle features to grant or revoke access without touching code. - Set dashboard defaults per role so operators land on the right system health widgets. These defaults drive the cards shown immediately after login.
- Save changes to persist them for the current tenant. Role edits never affect other tenants because each tenant maintains its own ACL matrix.
Assign user access
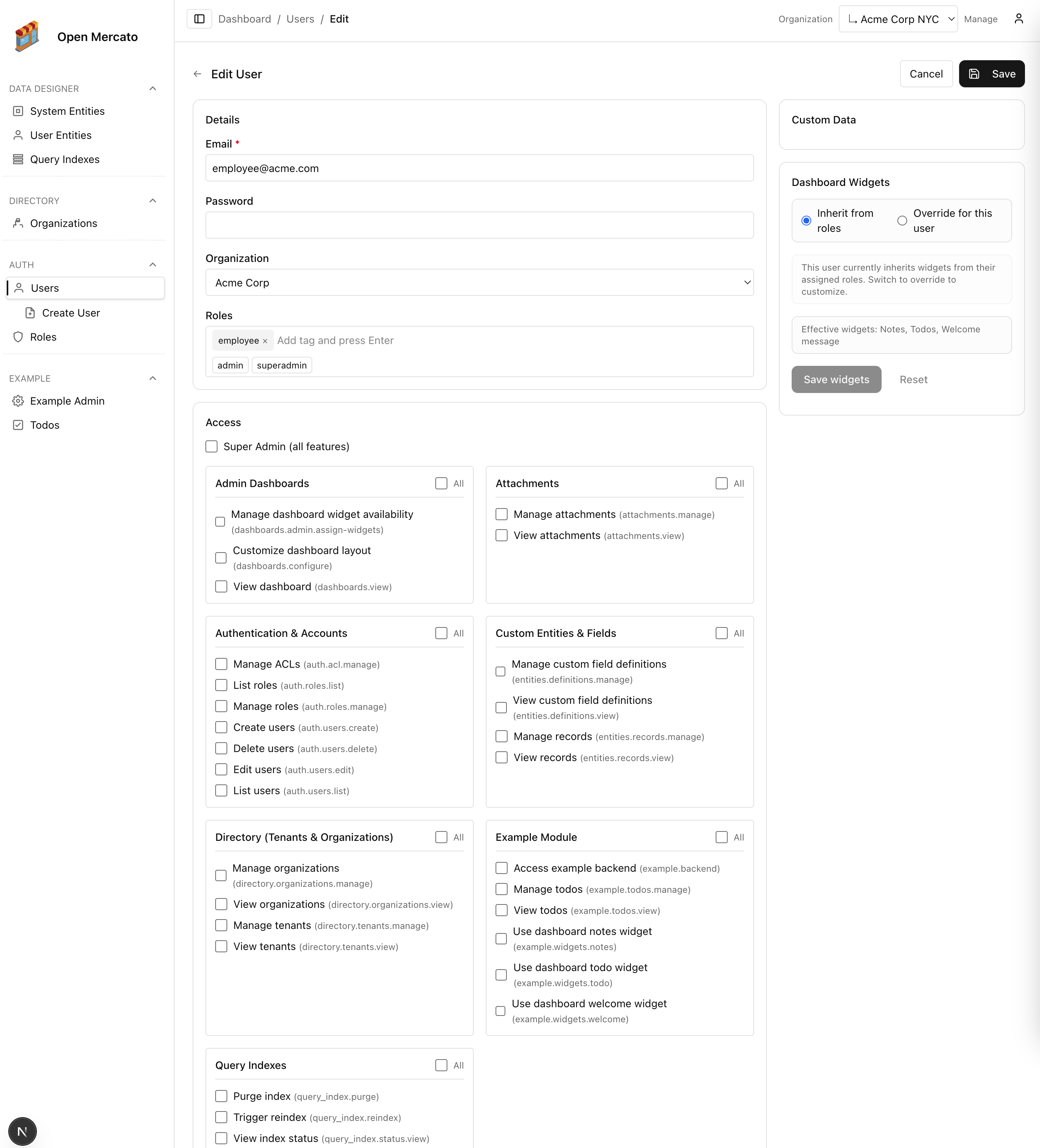
- Open Auth → Users to invite new operators or adjust identities. The users list respects the current organization and tenant scope.
- Select a user to edit their profile, assign roles, and apply per-user feature overrides. Overrides are additive—you can grant temporary features without cloning roles.
- Control dashboard widgets for individuals when you need tailored visibility. Per-user settings override the role defaults configured above.
- Reset access directly from this screen when operators forget credentials or need a password rotation.
Review and audit access
- Feature search helps confirm which roles expose sensitive functions like
directory.organizations.manageor module-specific create/edit permissions. - Organization scope is shown on every edit page so you know which branches a user can enter. Combine role features with organization visibility lists for fine-grained control.
- Keep records fresh by deactivating accounts instead of deleting them. Soft-deleted users retain audit history while preventing new sign-ins.
Next steps
- Learn more about RBAC internals and how features flow through the DI layer.
- Explore organization management to understand how scopes and visibility interact with user permissions.
- Return to the Login & authentication guide for the end-user sign-in experience.